Managed Security Services
Protect your business and your data with our managed security services.
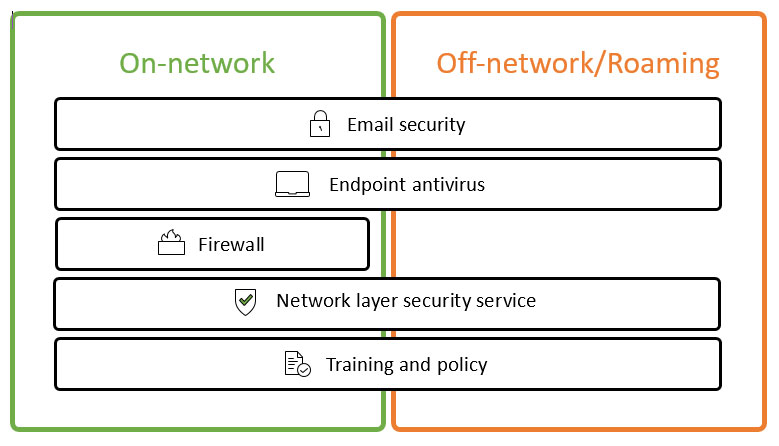
Security is about managing risk through layers. Our security services offer solutions for all the area's where IT security is a concern. Stop viruses, spyware, worms, Trojans, key loggers, and more before they enter your network, with all-in-one, comprehensive network protection.
Network and Security Assessment
Block threats before they enter your network with our Network and Security Assessment preformed regularly, we can see weak points and security concerns before the hackers do. Our Non-Intrusive assessments analyze every device on your network.
We provide a complete set of reports that touches on the broadest range of systems, network assets, settings, configuration, installed applications and endpoint security.
Security Assessment
- Security Risk Report
- Security Management Plan
- Computer Security Report Card
- Anomalous Login Report
- External Vulnerabilities Scan Detail Report
- External Vulnerability Scan Detail by Issue Report
- External Network Vulnerabilities Summary Report
- Outbound Security Report
- Security Policy Assessment Report
- Share Permission Report by Computer
- Share Permission Report by User
- User Behavior Analysis Report
- Login History by Computer Report
- Login Failures by Computer Report
- Data Breach Liability Report
Network Assessment
- Network Risk Report
- Network Management Plan
- Full Detail Report
- Site Diagram
- Asset Detail Report
- Full Detail Change Report
- Excel Analysis Export/Report
- Quarterly Business Review Report
- Backup & DR Needs Analysis Report

View a sample of the reports we will prepare for you!
Email Security
Essentials for Email Security
With our Email Security Gateway, protecting against inbound malware, spam, phishing, and Denial of Service attacks ensures that business productivity isn't impacted by attacks through the email system. Powerful and customizable policies enable further enforcement of detailed requirements that govern inbound email messages.
Email-Borne Threat Protection
Advanced Threat Protection helps keep email-borne attacks outside your networks and provides email continuity and data leakage protection.
Real-Time Analysis
Real-time detection for dynamic threat analysis with 24/7 updates and protection.
Endpoint Antivirus
Today's malware, being dynamic and often targeted, requires a multi-layered approach based on proactive and smart technologies. Award-winning antimalware without system slowdowns, plus remote administration.
We protect all of the most-used operating systems with the same level of functionality, leaving no potential entry point to your network unprotected.
Our powerful security management console gives us real-time information on the security state of your network, endpoints and mobile devices, including security and administration functionality that protects you against threats.
Firewall
Award-winning, enterprise-grade protection for SMBs and distributed enterprises in one cost-effective, centrally managed solution.
See Threats Before It's Too Late
In an increasingly unpredictable threat environment, security breaches are becoming harder and harder to detect. Malware, backdoors, and data loss routinely go unnoticed for months, and in some cases years at a time. When the breach is finally discovered, it is usually reported by an external party and rarely through an internal review.
Our unique approach to network security focuses on bringing best-in-class, enterprise-grade security to any organization, regardless of size or technical expertise. Ideal for SMB, midsize, and distributed enterprise organizations, our award-winning Unified Threat Management (UTM) appliances are designed from the ground up to focus on ease of deployment, use, and ongoing management, in addition to providing the strongest security possible.
Fundamental Security Services
- Intrusion Prevention - uses continually updated signatures to scan traffic on all major protocols, providing real-time protection against network threats, including spyware, SQL injections, cross-site scripting, and buffer overflows.
- Reputation-Based Threat Prevention - A powerful, cloud-based web reputation service that aggregates data from multiple feeds to provide real-time protection from malicious sites and botnets, while dramatically improving web processing overhead.
- URL Filtering - In addition to automatically blocking known malicious sites, our content filter delivers granular content and URL filtering tools to block inappropriate content, conserve network bandwidth, and increase employee productivity.
- Gateway AntiVirus - Leverage our continuously updated signatures to identify and block known spyware, viruses, trojans, worms, rogueware and blended threats - including new variants of known viruses. At the same time, heuristic analysis tracks down suspicious data constructions and actions to make sure unknown viruses don't slip by.
- Application Control - Allow, block, or restrict access to applications based on a user's department, job function, and time of day. It's never been easier to decide who, what, when, where, why and how applications are used on your network.
- Network Discovery - A subscription-based service for Firebox appliances that generates a visual map of all nodes on your network, making it easy to see where you may be at risk. It helps ensure only authorized devices are connected while detecting all open ports and protocols.
Advanced Security Services
- APT Blocker - uses an award-winning next-generation sandbox to detect and stop the most sophisticated attacks including ransomware, zero-day threats, and other advanced malware designed to evade traditional network security defenses.
- Data Loss Prevention - Prevent data breaches and enforce compliance by scanning text and files to detect sensitive information attempting to exit your network, whether it is transferred via email, web, or FTP.
- Threat Detection and Response - Security data collected from our appliance is correlated by enterprise-grade threat intelligence to detect, prioritize and enable immediate action against malware attacks.
- Access Portal - Access Portal provides a central location for access to cloud-hosted applications, and secure, clientless access to internal resources with RDP and SSH.
- Wireless Intrusion Prevention (WIPS) - WIPS has patented Marker Packet technology that reliably detects and classifies all APs and connected devices - such as smartphones and tablets - in or around your airspace as authorized, external, or rogue.

Network Layer Security Service
Accurately and continuously prevent and reduce the impact of malicious threats to your business anywhere your data goes. Protecting sensitive data is getting harder every day, as technology evolves and bad guys find new ways to steal sensitive data. Merging the big data security business operations required to do so is a balance between business priorities, budget pressures, and productivity requirements. It's a difficult task, made even more so when you don't have a dedicated IT security staff or ready access to security experts.
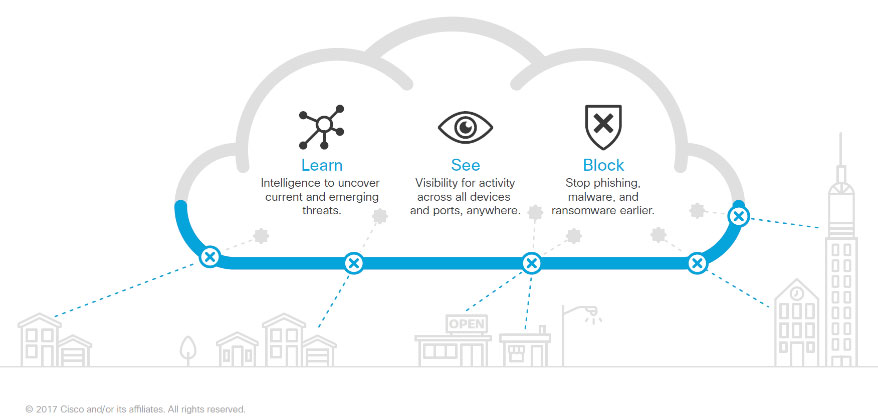
Our Cisco Umbrella Product Primers
-
First line of defense against threats:
Cisco Umbrella is built into the foundation of the internet and blocks requests to malicious/unwanted destinations before a connection is even established - without adding any latency. Stop threats over any port before they reach your network and endpoints. -
Intelligence to see attacks before they launch:
Cisco sees the relationships between malware, domains, IPs, and networks across the internet. Similar to Amazon learning from shopping patterns to suggest the next purchase, Umbrella learns from internet activity patterns to automatically identify attacker infrastructure being staged for the next threat. -
Roaming coverage / off-network protection:
Cisco Umbrella provides coverage wherever your users roam. We extend protection to laptops and users off the corporate network. And we deliver the same enterprise-grade security both on and off-network - identifying threats that firewalls and antivirus miss. -
Won't slow you down = security without sacrifices:
Simply put, we don't introduce anything new to the way the internet works. You currently use a recursive DNS provider through your ISP, but Cisco Umbrella does it faster, more reliably, and with a focus on security. -
Increase visibility into internet activity across all users and locations:
Your users and apps have left the perimeter. Cisco Umbrella provides the visibility needed to protect internet access across all devices on your network, all office locations, and roaming users. Our reports provide you with a more complete picture of real-time network usage, so that you can have data-supported conversations with your employees and your MSP about security risk management, usage, compliance, cloud services, and infections.
 Managed security services are becoming an increasingly popular option for increasing the value brought by security solutions while reducing IT complexity.
Managed security services are becoming an increasingly popular option for increasing the value brought by security solutions while reducing IT complexity.
Training & Policy

We offer the world's most popular integrated Security Awareness Training and Simulated Phishing platform. More than 15,000 organizations worldwide are using it. You now have a way to better manage the urgent IT security problems of social engineering, spear phishing and ransomware attacks.
-
Awareness Program Builder
Get your customized Automated Security Awareness Program with calendar and PDF. -
Phishing Security Test
Did you know that 91% of successful data breaches started with a spear-phishing attack? -
Phish Alert Button
Do your users know what to do when they receive a suspicious email or attachment? -
Domain Spoof Test
One of the first things hackers try is to see if they can spoof the email address of your CEO. -
Ransomware Simulator Tool
Is your network effective in blocking ransomware and social engineering attacks? -
Weak Password Test
Did you know 81% of hacking-related breaches used either stolen and/or weak password? -
Email Exposure Check Pro
Have your users made you an easy target for spear phishing? Find out now! -
Training Preview
You now really have 500+ new ways to make sure your users Think Before They Click!
At IT TechStop we believe in building lasting relationships with our valued customers. Contact us today to find out how Managed Security Services can benefit you and your business!
More Information about our IT assessment Schedule your free IT assessment today!
