Security Assessment Reports
- Security Risk Report
- Security Management Plan
- Computer Security Report Card
- Anomalous Login Report
- External Vulnerabilities Scan Detail Report
- External Vulnerability Scan Detail by Issue Report
- External Network Vulnerabilities Summary Report
- Outbound Security Report
- Security Policy Assessment Report
- Share Permission Report by Computer
- Share Permission Report by User
- User Behavior Analysis Report
- Login History by Computer Report
- Login Failures by Computer Report
- Data Breach Liability Report
 Security
Risk Report
Security
Risk Report
This report includes a proprietary Security Risk Score and chart showing the relative health (on a scale of 1 to 10) of the network security, along with a summary of the number of computers with issues. This powerful lead generation and sales development tool also reports on outbound protocols, System Control protocols, User Access Controls, as well as an external vulnerabilities summary list.
 Security
Management Plan
Security
Management Plan
This report will help prioritize issues based on the issue's risk score. A listing of all security related risks are provided along with recommended actions.
 Computer
Security Report Card
Computer
Security Report Card
The Computer Security Report Card assesses individual computers at a high level based on various security criteria. Devices discovered on the network are assigned an overall score, as well as a specific score for each of the assessment categories detailed in the report card. The scores are represented as color-coded letter grades ('A' through 'F'). The report card provides a relative measure as to how well a computer complies with security best practices.
 Anomalous
Login Report
Anomalous
Login Report
Expand your security know-how and easily identify anomalous user logins with a value-add report that methodically analyzes login history from the security event logs. The report uses mathematical modeling and proprietary pattern recognition to highlight potential unauthorized users who log into machines they normally do not access and at times they normally do not log in. This report delivers a security professional focus and pinpoints a manageable set of logins to investigate.
 External
Vulnerabilities Scan Detail Report
External
Vulnerabilities Scan Detail Report
A comprehensive output including security holes and warnings, informational items that can help make better network security decisions, plus a full NMap Scan which checks all 65,535 ports and reports which are open. This is an essential item for many standard security compliance reports.
 External
Vulnerability Scan Detail by Issue Report
External
Vulnerability Scan Detail by Issue Report
A more compact version of the External Vulnerability Scan Detail report that is organized by issues. Devices that are affected are listed within an issue. This report is useful for technicians that are looking to resolve issues, rather than performing remediation on a particular system.
External Network Vulnerabilities Summary Report
This report provides a priority ordered listing of issues by CVSS that allows technicians to prioritize the issues they are working on. It provides an extremely compact view of all issues allow a quick survey of the various issues that were detected in an environment.
 Outbound
Security Report
Outbound
Security Report
Highlights deviation from industry standards compared to outbound port and protocol accessibility, lists available wireless networks as part of a wireless security survey, and provides information on Internet content accessibility.
 Security
Policy Assessment Report
Security
Policy Assessment Report
A detailed overview of the security policies which are in place on both a domain wide and local machine basis.
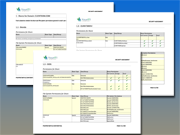 Share
Permission Report by Computer
Share
Permission Report by Computer
Comprehensive lists of all network “shares” by computer, detailing which users and groups have access to which devices and files, and what level of access they have.
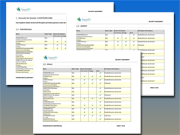 Share
Permission Report by User
Share
Permission Report by User
Organizes permissions by user, showing all shared computers and files to which they have access.
 User
Behavior Analysis Report
User
Behavior Analysis Report
Shows all logins, successful and failure, by user. Report allows you to find service accounts which are not properly configured (and thus failing to login) as well as users who may be attempting (and possibly succeeding) in accessing resources (computers) which they should not be.
 Login
History by Computer Report
Login
History by Computer Report
Same data as User Behavior but inverted to show you by computer. Quite useful, in particular, for looking at a commonly accessed machines (file server, domain controller, etc.) – or a particularly sensitive machine for failed login attempts. An example would be CEO’s laptop – or the accounting computer where you want to be extra diligent in checking for users trying to get in.
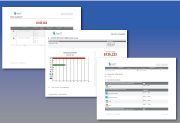
 Login
Failures by Computer Report
Login
Failures by Computer Report
Report identifies users who have succeeded in logging in to another machine. Great for auditing/logging purposes to know of all attempts.
 Data
Breach Liability Report
Data
Breach Liability Report
Identifies specific and detailed instances of personal identifiable information (PII) and cardholder data throughout a computer network that could be the target of hackers and malicious insiders. It also calculates the potential monetary liability
Network Assessment
- Client Risk Report
- Network Management Plan
- Full Detail Report
- Site Diagram
- Asset Detail Report
- Full Detail Change Report
- Excel Analysis Export/Report
- Quarterly Business Review Report
 Network
Risk Report
Network
Risk Report
This is the "money" report for you. The report presents your client with a summary of their overall risk score based on your scan, along with simple charts to show the problem areas. Each problem area represents an opportunity for you to present a proposed solution and pitch your services. The purpose of this report is for you to use as a "discussion document" to aid you in having a conversation with your customer about the specific risk areas you found, what they mean, and how you can help. Keep the Full Network Assessment in your hip pocket, and pull it out when your prospective new client asks how you came up with your findings!
 Network
Management Plan
Network
Management Plan
This report will help prioritize issues based on the issue's risk score. A listing of all affected computers, users, or sub-systems are provided along with recommended actions.
 Full
Detail Report
Full
Detail Report
Our scan will pull out literally hundreds of pages of end-user network activity and configuration data. The Full Network Assessment Report includes every detail, presented in line-item fashion in an editable report document. The report is organized by section with a table of contents to help you locate the specific findings of interest, and problem areas are conveniently highlighted in red, making it easy to spot individual problems to be rectified.
 Network
Assessment PowerPoint
Network
Assessment PowerPoint
Use our generated PowerPoint presentation as a basis for conducting a meeting presenting your findings from the Network Detective. General summary information along with the risk and issue score are presented along with specific issue recommendations and next steps.
 Site
Diagram
Site
Diagram
Once you sign up for Network Detective and run a scan, you'll have the option to generate a site diagram which breaks down and categorizes all of the assets available on the network. The schematic shows the basic network structure, with convenient drill downs into each group of like workstations. Each device is annotated with important identifying configuration information and is color-coded based on its status.
 Asset
Detail Report
Asset
Detail Report
For each network scan, this report provides detailed information on each of the individual assets discovered by Network Detective. The report is ideal for cataloging and documenting the complete settings and configurations for individual workstations and servers.
 Full
Detail Change Report
Full
Detail Change Report
Everyone knows that a computer network is a dynamic environment and as such is constantly changing. And a Network Assessment is only a snapshot of the network status at the time the assessment is run. That's why we include a valuable Network Assessment Comparison Report. Every time you run an assessment on a given network, the software generates a unique encrypted data file containing all the findings. Network Detective allows you to generate a report that compares the results of any two network scans, and highlights everything that has changed.
 Excel
Analysis Export/Report
Excel
Analysis Export/Report
We also give you the ability to output all of the assets and configurations uncovered by our scan, and export it into an Excel file format. Once in Excel, you'll be able to take the data and import it into your favorite Service Desk or PSA system, or simply create your own custom sorts, analyses, reports and graphs inside of Excel. Add columns of new data such as location info, emergency phone numbers, and customer instructions to make this report even more valuable.
 Quarterly
Business Review Report
Quarterly
Business Review Report
This report compares one time period to a previous one forming the basis for a Quarterly Business Review meeting. It centers on changes rather than detailed data and shows overall trending. Use this report to encourage "face-to-face" meetings and improve stickiness with your customers.
 Backup
& DR Needs Analysis Report
Backup
& DR Needs Analysis Report
Report presents an analysis of the Backup/Disaster Recovery needs for an environment. This report includes both discovered information regarding the storage needs of an environment along with analysis of both onsite and offsite backup requirements.
